Sophos ZTNA: The Modern Zero Trust Network Access Solution
In a world where the boundary between internal and external systems is increasingly blurred, traditional security models based on internal trust are becoming obsolete. Sophos ZTNA offers a new, robust approach to secure access in the age of sophisticated cyber threats.

1. Introduction to Sophos ZTNA
ZTNA (Zero Trust Network Access) is a modern security framework based on the principle of “Never trust, always verify.” Unlike traditional models that allow internal users unrestricted access, ZTNA requires strict authentication and device verification for every connection—regardless of location—before granting access to company resources.
Instead of treating the internal network as a “safe zone,” ZTNA assumes that no one—internal or external—is inherently trustworthy. Every access request undergoes continuous security checks and is limited to only the necessary resources.
Traditional VPNs: A wide-open door to modern threats.
2. VPN Security Vulnerabilities
VPNs allow remote users to access the company’s internal network by creating a secure “tunnel” between their device and the corporate system. However, VPNs cannot control threats originating from compromised user devices. If a device is infected with malware or spyware, VPNs cannot prevent these threats from spreading into the internal network. As a result, insider attacks become more dangerous, especially when devices are not thoroughly checked before connecting.

Traditional VPNs are outdated—upgrade to Sophos ZTNA for smarter, safer access!
3. Sophos ZTNA – The VPN Alternative
Sophos Zero Trust Network Access (ZTNA) is an advanced security solution built on the Zero Trust model—always assuming no one inside the network is automatically trusted. ZTNA ensures that before granting access to any resource or application, users must pass strict authentication and their devices must be verified as secure.

4. How Sophos ZTNA Works
- User Authentication: Users must log in to their corporate account and verify their identity before accessing any business resources.
- Device Health Check: ZTNA checks the security status of the user’s device—including malware detection and vulnerability assessment—before granting access.
- Granular Access Control: ZTNA only provides the minimum necessary access based on security policies and device status, reducing the risk of insider threats.

No more slow and insecure VPNs—Sophos ZTNA delivers fast, secure, and intelligent application access with Zero Trust.
5. ZTNA vs. VPN: Why ZTNA Stands Out
| Aspect | VPN | ZTNA |
|---|---|---|
| Security Approach | Assumes the corporate network is safe. Once connected, users have broad access, increasing risk if accounts or devices are compromised. | Based on Zero Trust—never trust, always verify. Every access request is thoroughly checked, and only necessary resources are accessible. |
| Access Control | Grants access to the entire internal network, which can enable threats to spread if a device or account is compromised. | Applies the “least privilege” principle—users and devices only access what they need, reducing attack surfaces. |
| User & Device Management | Cannot distinguish between users or devices; once connected, all resources are available without granular control. | Continuously monitors and authenticates both users and devices, checking OS versions, patches, and antivirus status to ensure only secure devices connect. |
| Scalability & Flexibility | Can become complex and inefficient to manage at scale, especially in cloud environments. | Designed for flexibility and easy scaling, especially as applications move to the cloud. |
| Threat Response Integration | Lacks integration with advanced security tools and cannot automatically respond to threats. | Integrates with Sophos Intercept X, XDR, and MDR for unified threat detection and rapid response. |
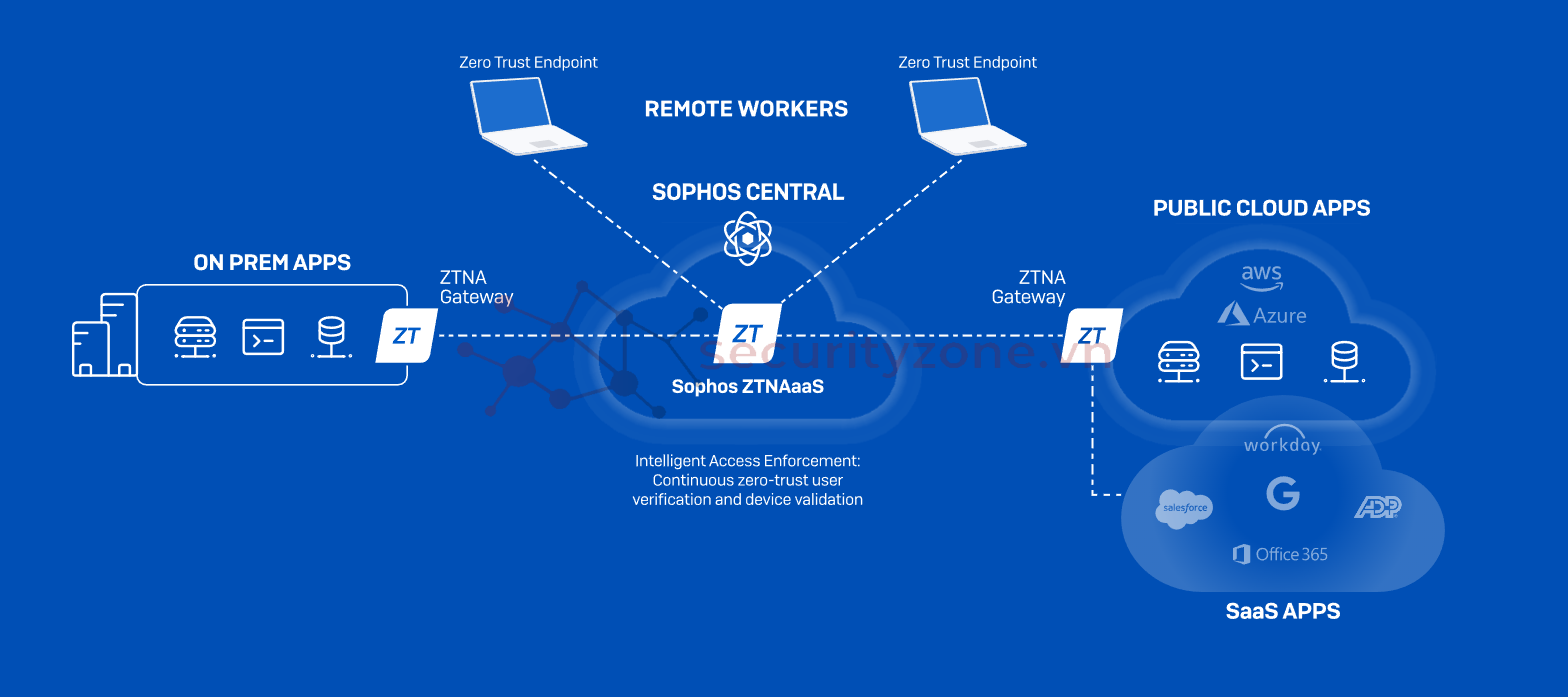
Zero Trust is no longer optional—it’s the new standard. Sophos ZTNA is the easiest way to implement it today!
6. Key Features of Sophos ZTNA
- Enhanced Security: Eliminates implicit trust in user devices, protecting the corporate network from malware threats that can bypass traditional VPNs. Only authenticated and secure devices are allowed access.
- Easy Management: Centralized management via Sophos Central makes deployment and policy control simple, without the need for multiple tools.
- Seamless User Experience: Users can securely access resources from anywhere without complex VPN setups, maintaining productivity and security.
- Deep Sophos Integration: Works with other Sophos products like Intercept X, Firewall, and XDR for real-time threat detection and response.
- Flexible, Cost-Effective Deployment: Cloud-based deployment reduces hardware costs and resources while maintaining high security. Managed via Sophos Central or fully supported by Sophos as needed.
No complex configurations, no multiple tools—just one agent with Sophos ZTNA for secure access control.
7. Conclusion
With superior security, easy management, and a seamless user experience, Sophos ZTNA is rapidly becoming the ideal replacement for traditional VPNs—especially in today’s remote work environment. ZTNA not only overcomes VPN limitations but also introduces a new, flexible, and effective approach to network security.
If your business is searching for a powerful, easy-to-manage security solution for remote work, Sophos ZTNA is the right choice to protect your company’s resources from evolving cyber threats.
Explore a hands-on ZTNA lab here.
